HOW TO PROTECT A SITE FROM SQL INJECTION!
 PROTECTION FROM SQL INJECTION
PROTECTION FROM SQL INJECTION
What Is Exactly SQL Injection?
SQL Injection is a technique used by the hackers to change SQL statements running at the backend from forged executed SQL commands. Such kind of injections is usually done through input fields of the form causing a bad effect on database. This results in loss of sensitive information from the database.Through such tactics, attackers input vulnerable data to SQL interpreter that executes unintended commands. By such PHP MySQL injections, attackers may insert, update or even delete data from database.
Web developers use different tactics and logic to find out vulnerabilities and their possible solutions. Nowadays you might have heard the term TDD and BDD. These both are development processes used in programming to assure the maximum security with testing while developing in different languages.
Back in 2017, around 50% malicious attacks on the web apps were based on SQL Injections. Source: AkamaiBut first, it is important to know what actually SQL Injection is and what harm it causes. But before let’s understand a few concepts.
| How You Can Prevent PHP SQL Injection Attacks |
|---|
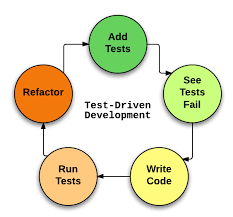
What is TDD?
Test Driven Development is a practice in which you write a test first and code later to pass the test. This approach makes sure that the number of bugs must be solved while development. The developer tightly writes the test cases first and then the code, as this practice enables him to quickly find out the potential bugs.The process is as follows:
- Write a test.
- Run the test (can fail).
- Write the code.
- Run the test again and see it pass.
- Refactor
What Is Exactly SQL Injection?
SQL Injection is a technique used by the hackers to change SQL statements running at the backend from forged executed SQL commands. Such kind of injections is usually done through input fields of the form causing a bad effect on database. This results in loss of sensitive information from the database.Through such tactics, attackers input vulnerable data to SQL interpreter that executes unintended commands. By such PHP MySQL injections, attackers may insert, update or even delete data from database.
Cause Of SQL Injection
While coding we should follow best practices to avoid SQL injection in PHP. Some of the causes which can affect these attacks are:- Incorrectly filtered space characters
- Incorrect Type handling
- Passing unsanitized data to DB
- Not using full Unicode encoding
- Mixing of the code and data.
- Use of quotation marks to delimit strings
Let’s See The Examples
The following PHP SQL injection example will help you better understand the concept of SQL injections:Example # 1
Suppose we have a form containing 2 text fields’ username and password, along with a login button. The backend PHP code will be as follows:In this way, the above query will be updated as:
Example # 2
The SQL query is a legitimate program. And we are creating such a program dynamically, by adding some data on the fly. This data can interfere within the program code and can even alter it, as every SQL injection example shows it (all examples in PHP/Mysql):|
|
Solutions to SQL injection vulnerabilities
The SQL injection protection in PHP is quite a complexed topic. In this post, I am demonstrating two methods through which you can solve this issue.Method 1
Now you need to make a few changes in the previous code. Make a function like:Method 2
Another approach for avoiding SQL injections is using PHP Prepared Statements. A prepared statement is a feature in PHP which enables users to execute similar SQL queries efficiently and repeatedly.Afterward, the application binds values to the parameters before finally executing the statement. This enables execution of the statement repeatedly with a different set of values.
Advantages of Executing Prepare Statements
- It reduces parsing time as the query is executed once but can be executed multiple times with the same parameters.
- Bound parameters reduce the bandwidth to the server because the whole query is not sent every time but the parameters are sending.
- Bound Parameters reduces the bandwidth as the whole query is not sent every time but parameters are sent.
Example
Consider the following example:Now consider line 15 containing bind_param. This function basically binds different parameters to the query and conveys parameters to the database. ‘sss’ is an argument which basically lists the type of data. Argument may be integer(i), double(d), string(s), BLOB(b). By telling the database what type of data to expect, we basically minimize risk of SQL injection.
Tips For Avoiding PHP SQL Injection Vulnerabilities
Prevention is better than cure. You must take the following precautions as these are the best ways to prevent SQL injection in php:- To avoid SQL injections, user input should be authenticated for a definite set of rules for syntax, type, and length.
- While giving administrative rights to the database to particular users, try to give the least rights in order to avoid any future attacks to sensitive data.
- If a user is given rights for a specific application, make sure that he does not access the application unnecessarily.
- Removing unused stored procedures may also help in the prevention of SQL injects.
- Be careful when using stored procedures as they are easily exploited.
Thanks for the guide!
ReplyDeleteThat was amazingly helpful
Wordpress Health Checkup