INTRODUCTION TO BLUETOOTH IN DIFFERENT WAY!

Now bluetooth is installed in all devices whether it is WINDOWS OR ANDROID OR MAC OR LINUX etc etc. by default
the ability to hack bluetooth can lead to serious leak of personal data (pics,call logs,media etc) and sending unwanted files to the victim or through the victim!
BLUETOOTH BASICS
Bluetooth is a universal protocol for low power, near field transmission operating at 2.4 to 2.485 GHz using spread spectrum , frequency hopping at 1600 hops per sec (*this value is a security measure*).
Minimum range for a bluetooth is 10m but there is no limit using a special antennas if can extent upto 100m or even more!
connecting of two devices referred as pairing . any two bluetooth devices can pair if they are discoverable . A discoverable bluetooth device transmit the following data.
1. NAME
2.CLASS
3. LIST OF SERVICES
4. TECHNICAL INFORMATON
When two devices connect they share a pre-shared pin for pairing and which is stored for future identification and pairing of device.
Each bluetooth device have a 48-bit identifier (like a MAC-Address) and a manufacutrer alloted name.
although recently process of pairing is much more secure but everyone has some kind of vulnerability >_<
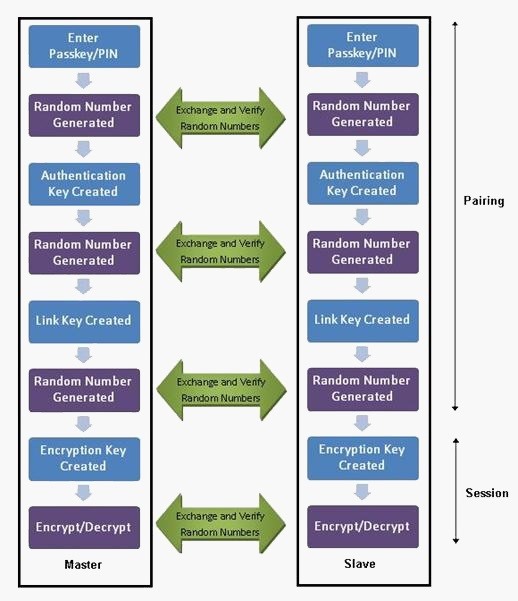
have a look through by this Daigram
Bluetooh device creates a piconet or a very small net ( in piconet there is one master and upto 7 slaves) because bluetooth uses frequency hopping so there device interfere is not possible because chances of 2 devices having same freq is very small.
BASIC LINUX TOOLS
The suit we will be using in linux for bluetooth is BlueZ.
BlueZ have essentially many tool which we can use to test and eventually hack bluetooth.
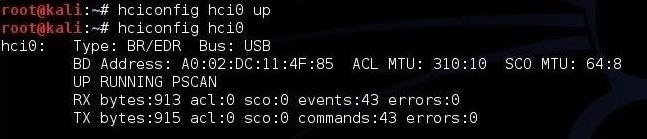
1. hciconfig -> This tool operates very similar to the ifconfigin linux . the difference is .it works and shows info of blueooth as shown in screenshot below
2. hcitool -> this is a enquiry tool. this shows info like device name, Device id , device class and device clock.
3. hcidump -> this tool enables us to sniff bluetooth connections.
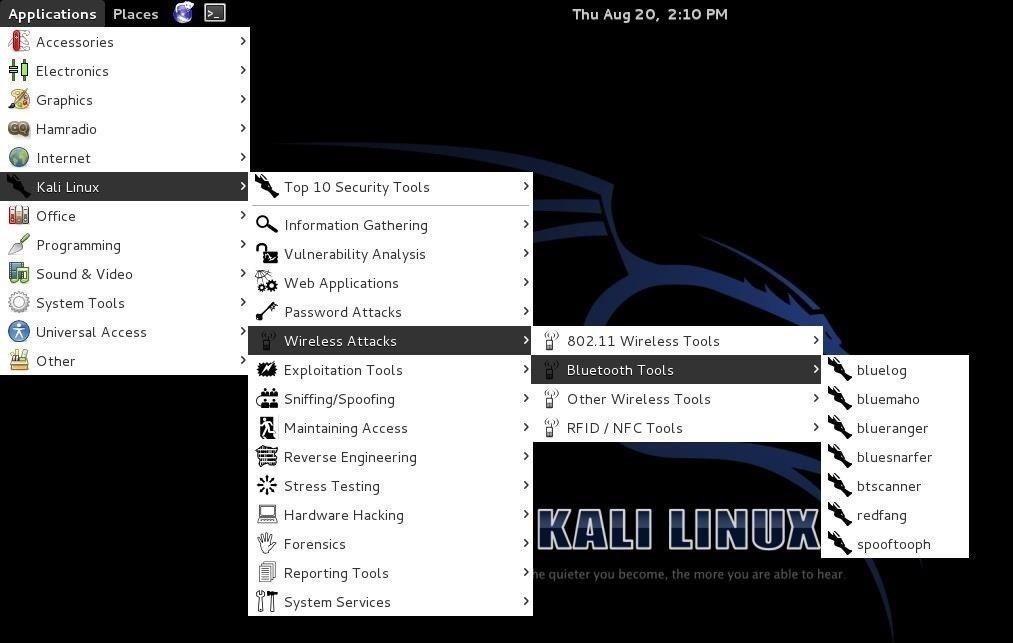
HACKING TOOL IN KALI
In kali there are some bluetooth testing tool installed by default . you can access them by
application -> wireless attacks -> Bluetooth tools
Several tools are there lets take a brief look at them
1. bluelog -> a bluetooth site survey tool, it scans the area for discoverable bluetooth devices and them log them in a file.
2. bluemaho -> A gui based suite of tool used for testing bluetooth.
3. blueranger -> A python script using i2cap pings to calculate the approx distance of bluetooth device .
4. btscanner -> GUI based bluetooth devices scanner.
5. Redfang -> tool to discover hidden bluetooth devices .
6. spooftooph -> bluetooth spoofing tool
3.BLUEBUGGING - Attacker is able to take over the victim smart phone.
1. bluelog -> a bluetooth site survey tool, it scans the area for discoverable bluetooth devices and them log them in a file.
2. bluemaho -> A gui based suite of tool used for testing bluetooth.
3. blueranger -> A python script using i2cap pings to calculate the approx distance of bluetooth device .
4. btscanner -> GUI based bluetooth devices scanner.
5. Redfang -> tool to discover hidden bluetooth devices .
6. spooftooph -> bluetooth spoofing tool
SOME BLUETOOTH ATTACKS
1. BLUEPRINTING - the process of footprinting.
2. BLUESNARFING - this attack takes data from a bluetooth enabled device. such as call logs,sms,images,calendar info.etc
3.BLUEBUGGING - Attacker is able to take over the victim smart phone.
4.BLUESMACK- DOS attack against bluetooth devices.
COMMENT DOWN IF GOT ANY ISSUE OR CONTACT ME !


Comments
Post a Comment